Get Autopilot Hash with Intune
25. Februar 2024 1 Kommentar
Often it is required to get the Autopilot hardware hash of already existent devices. This method is based on a simple PowerShell script that is assigned to all Windows devices.
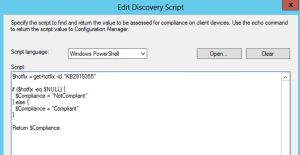
Create a PS1 file with the following content.
$bios=Get-WmiObject -class win32_bios
$devdetail = Get-WMIObject -Namespace root/cimv2/mdm/dmmap -Class MDM_DevDetail_Ext01
# $devdetail.DeviceHardwareData
# $bios.SerialNumber
$APCSVL1 = "Device Serial Number,Windows Product ID,Hardware Hash `r`n" + $bios.SerialNumber + ",," + $devdetail.DeviceHardwareData
$APCSVL1
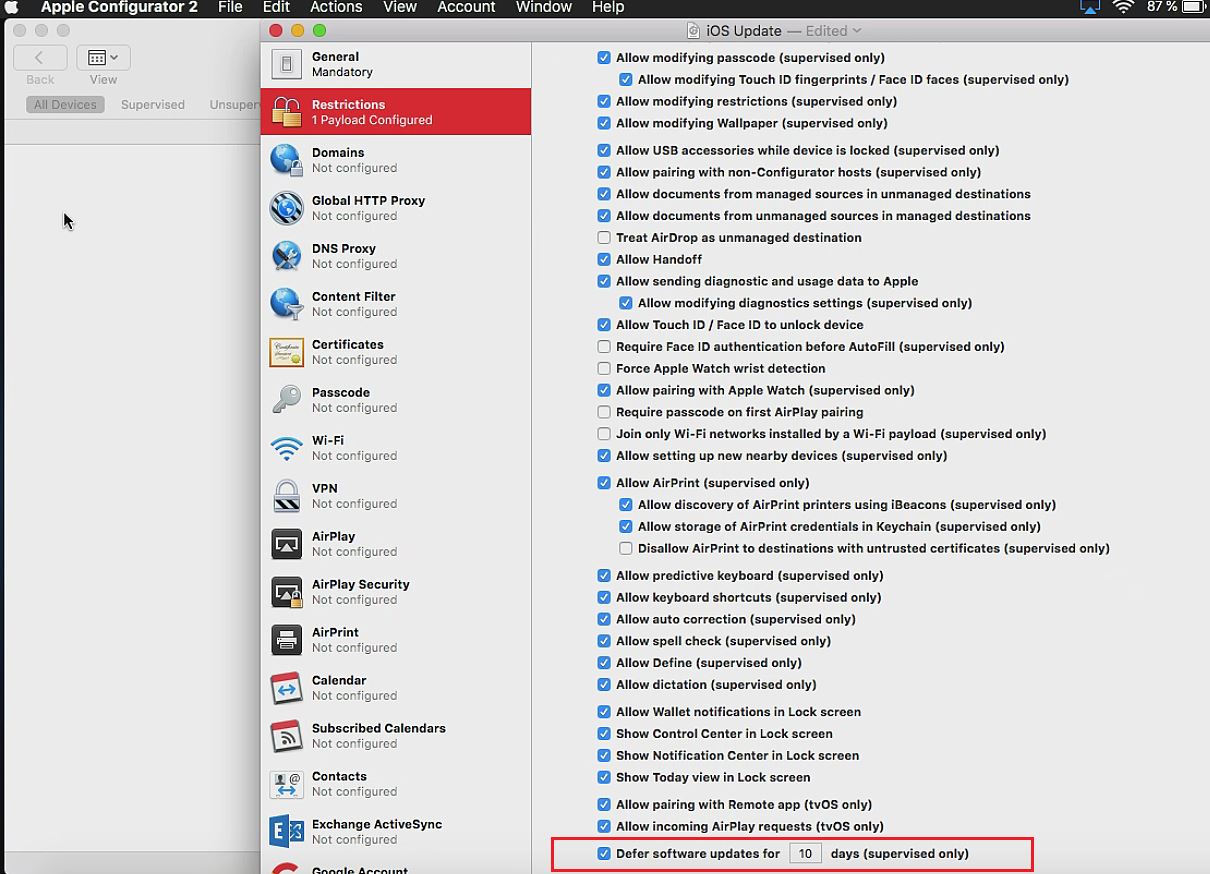
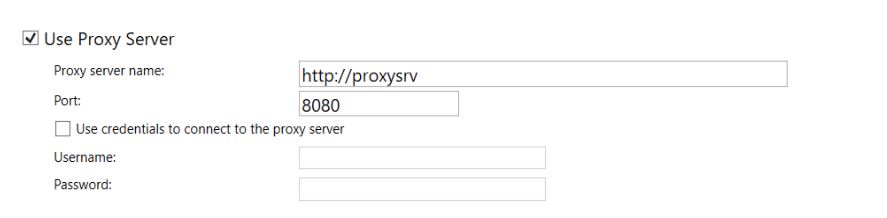
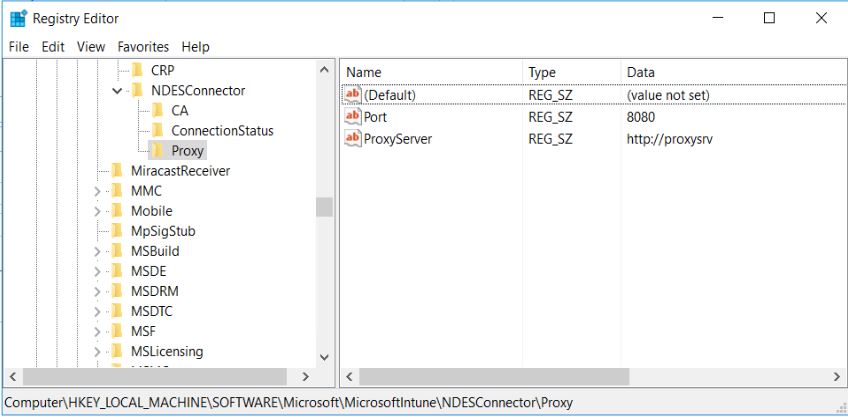
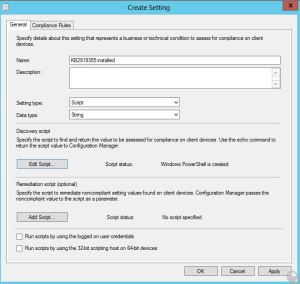
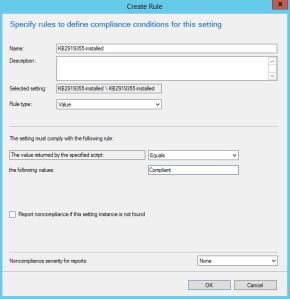
Add it as a „Platform script“, configure the following settings and assign it to all devices or a group of devices.
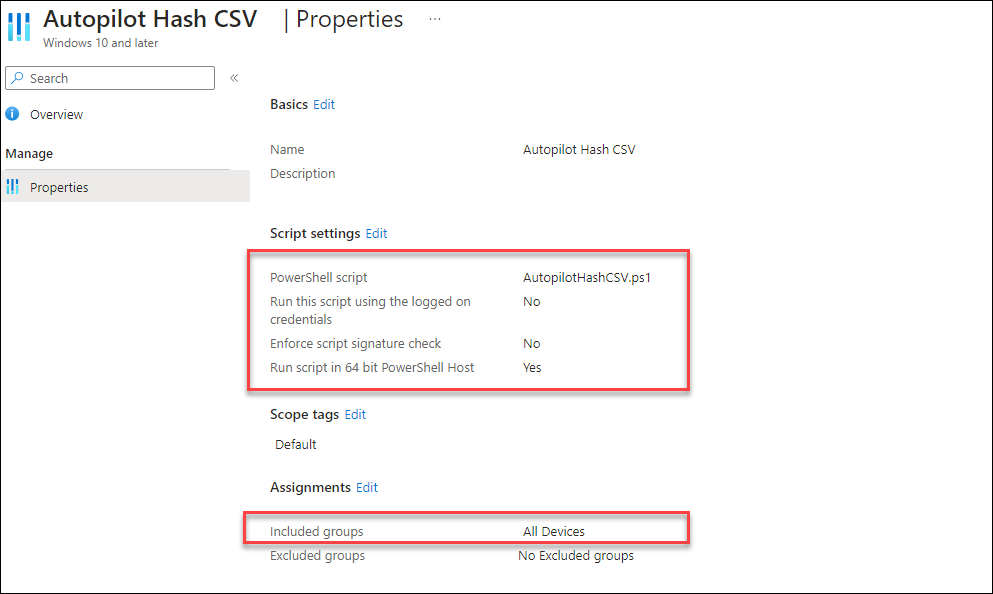
Record the script id.

Wait till your devices completed running the script. You can use Graph Explorer to verify if some devices already reported results. Use the following query. Remember the script id and modify your query accordingly.
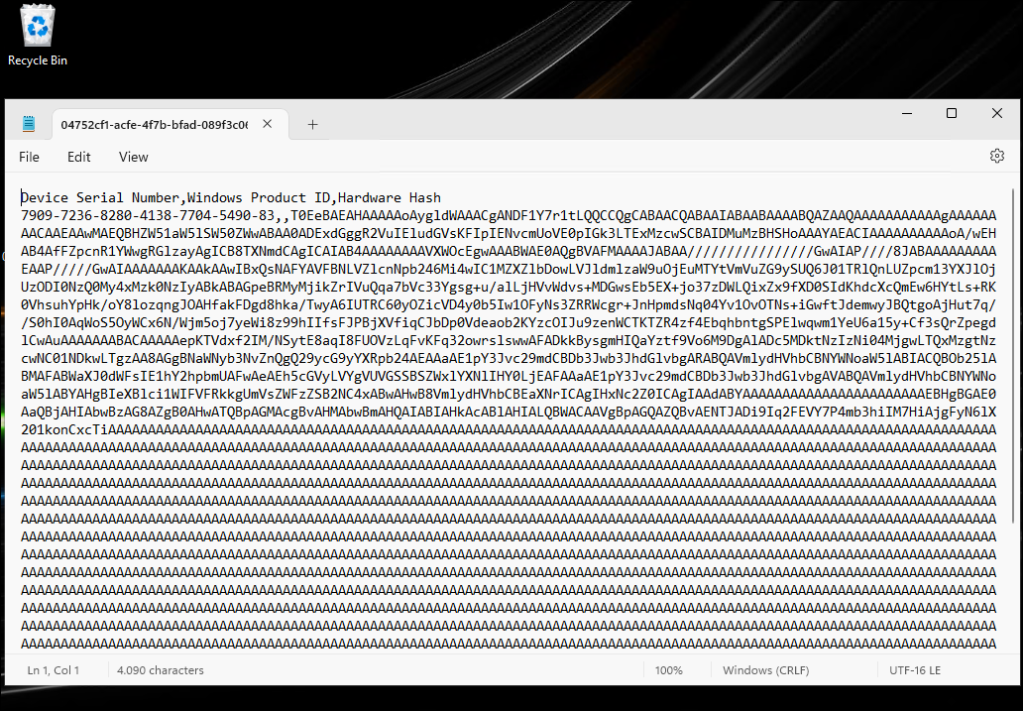
https://graph.microsoft.com/beta/deviceManagement/deviceManagementScripts/75566463-e3c5-4bab-bfbe-e53d03aa5ff6/deviceRunStates?$expand=managedDeviceThis example shows the PowerShell script output already containing the required data to create a CSV file. If you want a quick result just copy out the data and create a CSV file with the „resultMessage“ as content.
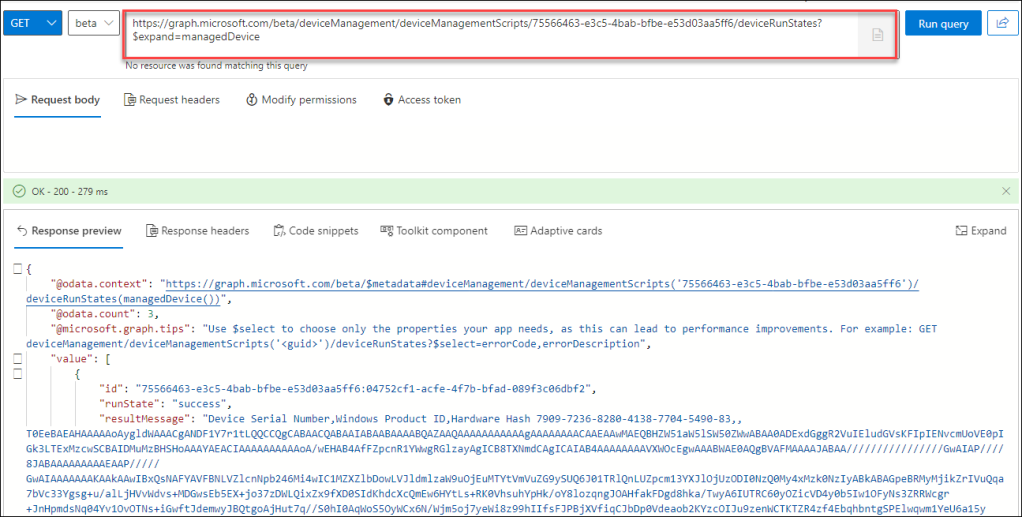
But we can get a step further and use Graph API to create the CSV file. This is a simple script snippet to create the file. We need the script id and the device id to find the matching data. The device id can be seen in the hardware blade of the device in the Intune Admin Center.
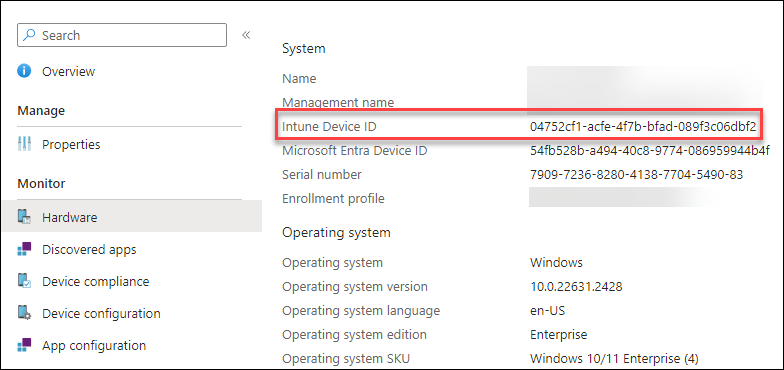
The script imports the Graph Modules and a simply loops through the results to find the matching device. If a device was found it exports the CSV file to the working directory. Use PowerShell ISE to run the lines in groups or one by one to see what’s happening.
install-module microsoft.graph
Install-Module Microsoft.Graph.Beta.DeviceManagement
Set-ExecutionPolicy Unrestricted -Scope Process -Force
connect-mggraph
$scriptid = "75566463-e3c5-4bab-bfbe-e53d03aa5ff6"
$deviceid = "04752cf1-acfe-4f7b-bfad-089f3c06dbf2"
$queryid = $scriptid + ":" + $deviceid
$queryid
# Get-MgBetaDeviceManagementScriptDeviceRunState -DeviceManagementScriptId $scriptid
$results = Get-MgBetaDeviceManagementScriptDeviceRunState -DeviceManagementScriptId $scriptid
foreach ($device in $results)
{
if ($device.id -eq $queryid)
{
write-host Device $deviceid found
$filename = $deviceid + ".csv"
$device.ResultMessage | out-file -FilePath $filename
}
}Using a filter query is not working with the PowerShell cmdlet for whatever reason, maybe caused by the beta module. I used the foreach loop to step through the results.
End result is a CSV file named „deviceid.csv“ containing the hardware hash and ready made to import it into Autopilot with the Intune Admin Center.
Happy Autopiloting …