Intune Certificate Connector Proxy Issues
10. August 2018 4 Kommentare
We are in the process of implementing the necessary infrastructure for certificate deployment with Intune as documented here.
https://docs.microsoft.com/en-us/intune/certificates-scep-configure
The environment is highly secured, means that the certificate connectors outbound internet connection has to be configured with an outgoing proxy server. So, no problem we thought, since the connectors setup UI has a built-in configuration option for configuring the proxy server.
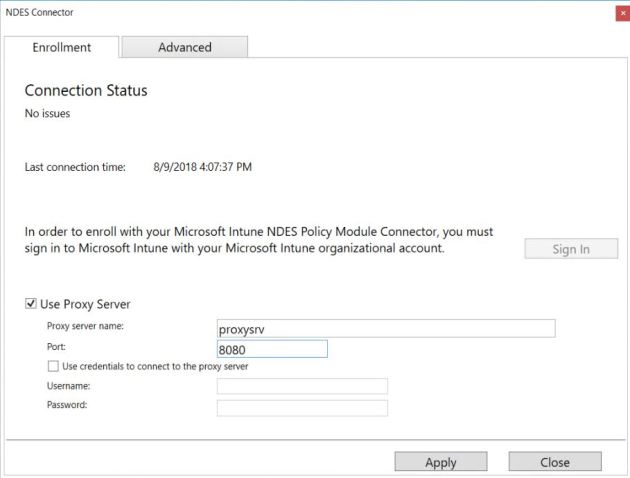
But the connector status in the Azure portal stays „red“ and there was no communication from the connector to Azure. We started troubleshooting and opened the connector UI again to verify that we entered the correct proxy server.
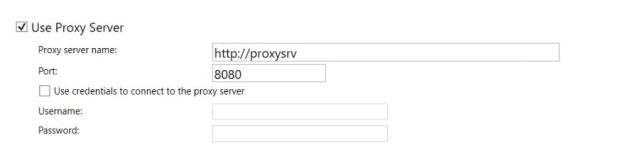
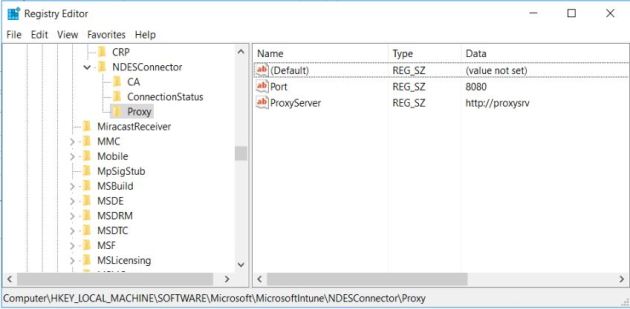
We wondered why the proxy server name was prefixed with „http: //“ since we didn’t entered that. Seems to be a kind of feature to add it automatically. The connectors configuration in the Windows registry contains this prefix too. We removed the prefix in the registry and restarted the service but it didn’t change the behaviour.
This blog https://ronnydejong.com/2017/05/02/part-2-deploying-microsoft-intune-connector-in-an-enterprise-world-troubleshooting/#more-4326 shows the usual troubleshooting options, log files and tools to format the logs.
The connector log was showing:
Exception in version sync thread: System.ArgumentException: Location Service Error: https://manage.microsoft.com/RestUserAuthLocationService/RestUserAuthLocationService/Certificate/ServiceAddresses : CN=12343212-1234-4567-6789-123454321234 : System.Net.WebException: The remote name could not be resolved: manage.microsoft.com at System.Net.HttpWebRequest.GetResponse
Next idea was to try with a system proxy to get all SYSTEM processes in the direction to the proxy.
netsh winhttp set proxy proxysrv:8080 bypass-list="<local>" Current WinHTTP proxy settings: Proxy Server(s) : proxysrv:8080 Bypass List : <local>
But unfortunately this changes nothing in the game.
It’s starting to be curious and as a kind of last resort we wanted to check internet access oneselfs. So we started a browser session with „psexec“.
psexec -s -i "%programfiles%\Internet Explorer\iexplore.exe"
After configuring the proxy settings in the browser session we were able to access the URL „https://manage.microsoft.com“. So we are sure that the connection is possible and all internal rules are inplace and working.
This change is recorded in the default user profile (HKU\.DEFAULT) and used for a browser session in system context.
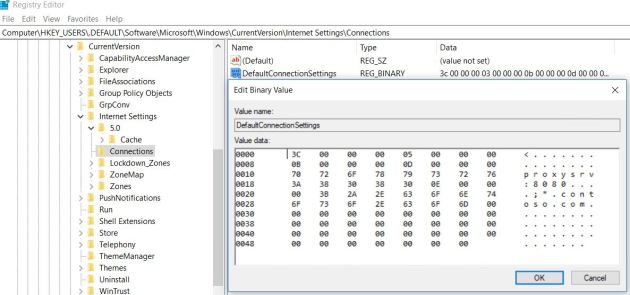
And oh wonder, the certificate connector was connecting successfully to Azure. Seems that this action was the magic change to get it working. It’s not clear at the moment why the proxy configuration setting in the connector properties is not working.
After some digging around we found an easy method to configure the systems proxy with „bitsadmin“ (https://docs.microsoft.com/de-de/windows/desktop/Bits/bitsadmin-tool)
bitsadmin /util /setieproxy localsystem MANUAL_PROXY proxysrv:8080 "<local>"
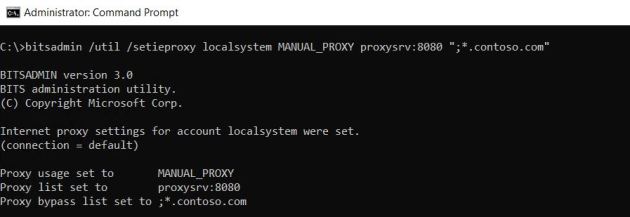
We will go productive now with this scenario…..
Thanks for the tip. Saved my day – was working on several Intune-connector issues last days, this was the last (and most difficult one)
glad it helped 🙂
Thanks for the tip as well. It also fixed the problem for me. 🙂
cool 🙂